Eset’s
full security arrangement against infections, spyware, worms and different
sorts malware, maintained by individual firewall, antagonistic to spam, hostile
to robbery and parental control, among various modules.Here we will share with
you How to active eset internet security with eset keys, eset nod32 username
secret key and will share workable most recent eset keys, eset nod32 username
password.
full security arrangement against infections, spyware, worms and different
sorts malware, maintained by individual firewall, antagonistic to spam, hostile
to robbery and parental control, among various modules.Here we will share with
you How to active eset internet security with eset keys, eset nod32 username
secret key and will share workable most recent eset keys, eset nod32 username
password.
Setup customization and clear UI
In
the midst of installation, it is possible to either empower or debilitate
location of PUPs (conceivably undesirable applications), change proxy settings
and set the strategy for overhauling program parts and restarting Eset right
from that point.
the midst of installation, it is possible to either empower or debilitate
location of PUPs (conceivably undesirable applications), change proxy settings
and set the strategy for overhauling program parts and restarting Eset right
from that point.
Sagacious
Security consolidates personal’s fire-wall
to supplant Windows Firewall & it’s can be set to program, instinctive,
approach based or learning mode. Clients may mystery key ensure the arrangement
settings for the circumstance the PC is granted to others.
Security consolidates personal’s fire-wall
to supplant Windows Firewall & it’s can be set to program, instinctive,
approach based or learning mode. Clients may mystery key ensure the arrangement
settings for the circumstance the PC is granted to others.
Malware confirmation through different scan techniques
Smart
Scan runs Eset’s predefined game plan to chase just standard system regions
down malware, Custom Scan gives customers the probability to look at zones and
settings, while Removable Media Scan just checks removable limit gadgets like
USB circles and DVDs.
Scan runs Eset’s predefined game plan to chase just standard system regions
down malware, Custom Scan gives customers the probability to look at zones and
settings, while Removable Media Scan just checks removable limit gadgets like
USB circles and DVDs.
Scanner arrangement and different settings
Also,
as sifting course of action is concerned, customers may select inside and,
pertinent menu or Smart breadth, and furthermore set the scanner to simply
recognize corrupted records without evacuating them. Moved settings may be
altered with respect to the compass objects (working memory, boot zones,
messages, reports and self-isolating accounts, runtime packers), heuristics and
Smart imprints, cleaning level, record extensions, size purposes of control,
substitute data streams, logging, Smart advancement, and establishment looking
at. Settings may be restored to default.
as sifting course of action is concerned, customers may select inside and,
pertinent menu or Smart breadth, and furthermore set the scanner to simply
recognize corrupted records without evacuating them. Moved settings may be
altered with respect to the compass objects (working memory, boot zones,
messages, reports and self-isolating accounts, runtime packers), heuristics and
Smart imprints, cleaning level, record extensions, size purposes of control,
substitute data streams, logging, Smart advancement, and establishment looking
at. Settings may be restored to default.
Additional
options can be intended for the persistent guard, HIPS, gamer mode, hostile to
stealth assurance, web access, email client, and against phishing.
options can be intended for the persistent guard, HIPS, gamer mode, hostile to
stealth assurance, web access, email client, and against phishing.
The highlights in Smart Security
Appeared
differently in relation to NOD32 Antivirus, Smart Security incorporates an
individual firewall, against spam module to channel suspicious or undesirable
messages, antagonistic to theft for scratch pads (requires enlistment, free),
nearby a parental control module to limit children’s passageway on the PC. Each
of these parts can be planned furthermore deactivated and re-enabled with a
solitary tick.
differently in relation to NOD32 Antivirus, Smart Security incorporates an
individual firewall, against spam module to channel suspicious or undesirable
messages, antagonistic to theft for scratch pads (requires enlistment, free),
nearby a parental control module to limit children’s passageway on the PC. Each
of these parts can be planned furthermore deactivated and re-enabled with a
solitary tick.
Performance & conclusion
Eset
is known not incredible results with respect to contamination disclosure
extent, sifting pace, and resources use. Sharp Security fulfills its name,
giving customers distinctive layers of security against e-threats while
investigating the web or yielding PC access to various customers. The people
who haven’t found the chance to test it are welcome to endeavor the av utility
for themselves.
is known not incredible results with respect to contamination disclosure
extent, sifting pace, and resources use. Sharp Security fulfills its name,
giving customers distinctive layers of security against e-threats while
investigating the web or yielding PC access to various customers. The people
who haven’t found the chance to test it are welcome to endeavor the av utility
for themselves.
System Requirements
ESET
Smart Security, 2015 discharge continues running on any framework with
Microsoft®
Smart Security, 2015 discharge continues running on any framework with
Microsoft®
Working System:
Windows®
10, 8.1, 8, 7, Vista, XP, and Microsoft Windows Home Server 2003, 2011.
(Against Theft not accessible for Home Servers).
10, 8.1, 8, 7, Vista, XP, and Microsoft Windows Home Server 2003, 2011.
(Against Theft not accessible for Home Servers).
Item
requires an Internet connection.
requires an Internet connection.
Installation Process:
Download
Eset with your system requirement. In
the event that your operating system is 64bit then download Eset shrewd
security for 64-bit & if you’re operating system is 32-bit then
download Eset savvy security for 32bit.
Eset with your system requirement. In
the event that your operating system is 64bit then download Eset shrewd
security for 64-bit & if you’re operating system is 32-bit then
download Eset savvy security for 32bit.
Eset smart security Activation key, eset nod32 username password:
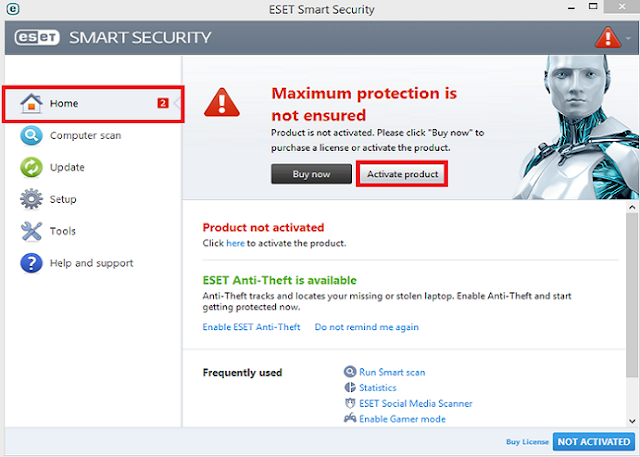
- Open Eset and snap on “Home” in left
sidebar then tap ‘activate Product’.
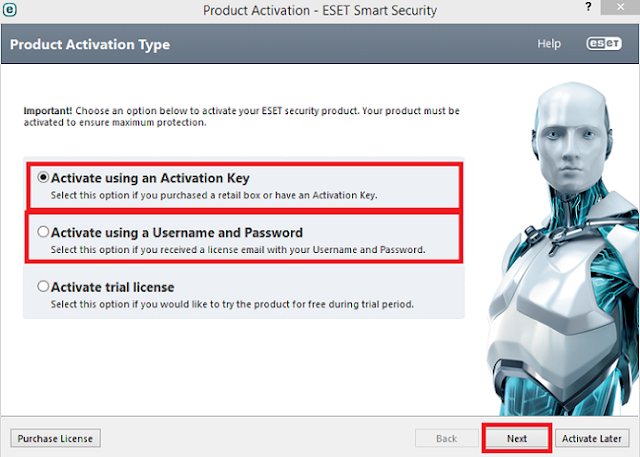
- Presently
select one of the option ‘Activate utilizing an Activation key” or
Activate utilizing a Username and Password’. Then Click on ‘Next’.
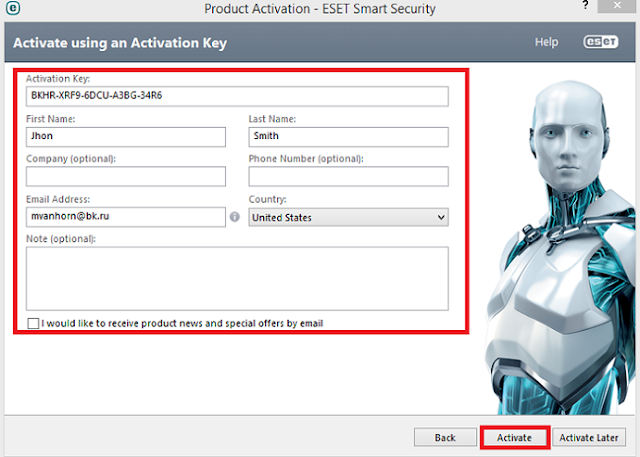
- On
the off chance that you choose the 1st option then fill in structure as like
the picture roar and on the off chance that you choose the 2nd option then fill
in form with eset keys, username & password. Then tap on ‘Activate’.
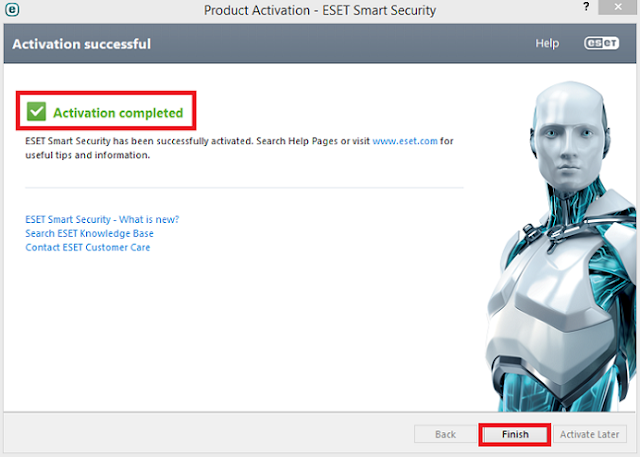
- Now
you will see a message ‘Activation Completed’. Click on ‘Finish’.
If you face any problem comment here. We will solve it.